2012 was a busy year for computer malware creators and security experts alike. A great number of computer infections were released last year, but there were three groups of computer threats that stood out the most. These were System Progressive Protection, a multi-name fake antivirus from Braviax family and Ukash virus ransomware infection with its most prominent version called FBI Moneypak virus. None of these infections is absolutely new. They all come from certain groups of computer threats that are periodically re-released, and thus we can presuppose that we will once again see new variations of these infections in 2013 as well.
Win 7 Security 2013 and others
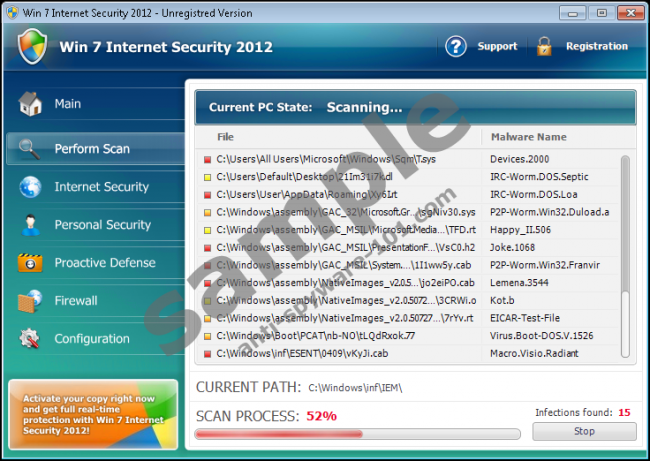
The Braviax family multi-rogue has been known since as early as 2008. It is a chameleon fake antivirus program that acquires a name after the infection takes place. When the malicious file gets into the system, it checks what version of the OS is installed on the compromised computer. Then it adapts the name and an interface that corresponds with the operating system. The most current version of Braviax rogue had such titles as Win 7 Security 2013, Win 7 Total Security 2013, Win 7 Home Security 2013, Vista Anti-Virus 2013, XP Internet Security 2013 and so on.
Fake antivirus programs from this family always use Anti-virus, Anti-Spyware, Home Security, Total Security, Security and Internet Security in their titles. The titles only vary according to the operating system and the issue (date) of the fake antivirus. Therefore, Vista Internet Security 2011, XP Internet Security 2012 and Win 7 Security 2013 all belong to the same family, and they were released at a different time. Braviax family rogues seem to be released every six months. It can be backed up by the search trend data that shows search peaks for XP Security 2013 in June and December 2012.
Infection behavior
Win 7 Security 2013 and its other variants are installed on the target computer via corrupted websites that exploit such system vulnerabilities as outdated applications. They also commonly use Trojans to spread globally. During the installation these fake antivirus programs configure registry in a way that allows them to startup automatically together with the operating system. Then it pops up onto the user’s screen, and due to its interface, Win 7 Security 2013 or any other Braviax rogue looks like a supplementary part of the system.
These rogues exhibit a generic fake AV behavior in a way that they perform a fake system scan, flood user with fake security alerts (most of which are shared and displayed by all versions of Braviax infections), and interfere with main system operations. That is to say, Win 7 Security 2013 and others can block legitimate executable files and display automated message on a web browser that says the program is infected and it needs to be shut down. The bright side is that, these multi-names are always outsmarted by security experts, and computer safety websites offer manual registration serial codes almost immediately after the release of the rogues. These codes differ with every new edition of Braviax infections, but they effectively accelerate the rogue removal process.
Tendencies for 2013
Keeping in mind, that Win 7 Security 2013 appeared approximately six months after the last issue of Braviax infections, we can expect Win 7 Security 2014, XP Internet Security 2014, Vista Anti-Virus 2014 in the first half of 2013. There might also be a new variation of this fake AV for Windows 8, so users of the new operating system have to be careful.
System Progressive Protection
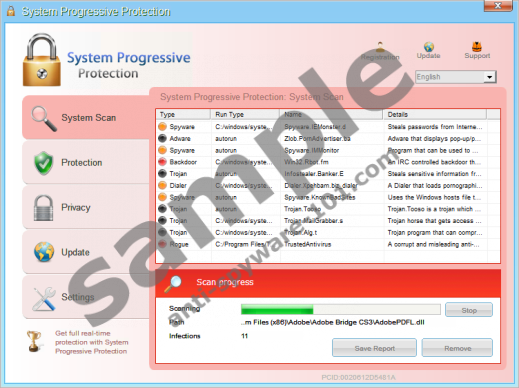
System Progressive Protection is a new edition of Winwebsec fake antivirus. Distinctive rogues from this group have been infecting computers worldwide for almost five years now. The most prominent names include Live Security Platinum, MS Removal Tool, Security Tool and others. System Progressive Protection was first released in September and then spread in the speed of light in October 2012. Just like all fake AVs System Progressive Protection aims for the money as it floods user with tons of fake security notifications.
Installation
During the installation System Progressive Protection generates random hexadecimal characters (usually 32) for its file names and then copies itself to %common_appdata% directory. Then it changes values for certain registry keys to make itself startup automatically. System Progressive Protection exhibits a type of behavior that is also common to legitimate programs. For example, it creates a shortcut icon on your desktop, adds a start menu entry and adds itself to the list of Add/Remove Programs in Control Panel.
Process termination
After the installation System Progressive Protection performs a full system scan and presents a report that says the computer is infected with multiple malware and the user is told to pay money register System Progressive Protection to protect his computer from threats. The rogue also displays an extensive list of false pop-ups and terminates a number of processes, displaying a message that says the file is infected. However, System Progressive Protection avoids terminating a few processes, including csrss.exe, explorer.exe, iexplorer.exe, rundll32.exe and others. Any processes that are related to Windows Update, Windows Security Center and Microsoft security products will be stopped by System Progressive Protection as well.
Defense mechanism
Then System Progressive Protection goes further to block Windows Firewall, Windows Defender and Windows Security Center whenever the user tries to open them. The fake AV monitors all main browsers and blocks user from accessing websites that might contain malware removal information. Whenever the user is blocked from accessing the Internet, System Progressive Protection displays a message that says the program or the web page is infected.
However, just like the Braviax family rogues, System Progressive Protection can also be registered manually with an activation key that is available at computer security websites. Although activation does not remove System Progressive Protection, it renders the rogue powerless and it is a lot easier to delete it from the infected computer.
Tendencies for 2013
Over the years Winwebsec proved to be a very intrusive and persistent group of fake antivirus programs. New editions of such rogues as System Progressive Protection appear sporadically, and without a particular pattern. For example, System Progressive Protection appeared in October 2012, while previous editions were released in February (Smart Protection 2012), April (Smart Fortress 2012), and August (Live Security Platinum). Obviously, we haven’t seen the last of Winwebsec rogues yet. It wouldn't be surprising to encounter a new version of Winwebsec group malware in the first quarter of 2013.
FBI Moneypak (Ukash virus)
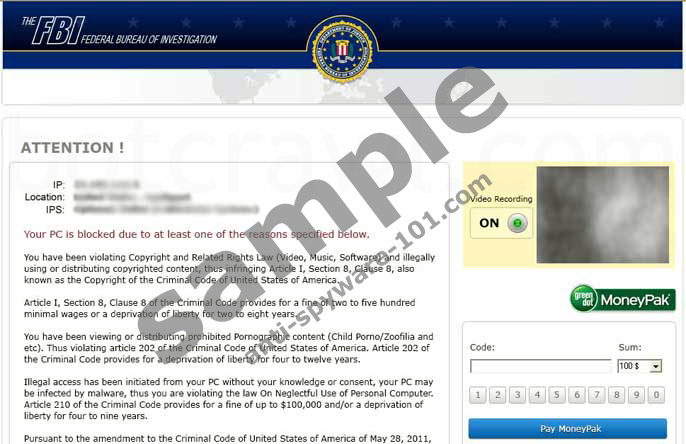
With the highest activity peak in July 2012 Ukash viruses, that are mostly distributed by Trojan Reveton, still remain an extremely group of infections even in the first half of 2013. Despite the fact that FBI Moneypak and other Ukash viruses also aim to rip easy financial gain, unlike System Progressive Protection and the Braviax family multi-rogue these computer threats are not fake antivirus programs. FBI Moneypak and others are screen-locking ransomware programs that blocks desktop access and ask for a particular ransom fee.
Ukash viruses target users in various countries and there are multiple versions for each location, displaying the fake notification in a particular language. The localized message displayed by the ransomware infection covers entire page and it displays a notification that is adorned by the official symbols of local law enforcement office. Users are asked for a payment because they supposedly are in possession of illicit material. Aside from FBI Moneypak other prominent names include Metropolitan Police Virus, BUNDESPOLIZEI Virus, GVU Virus and so on.
Infection
These computer threats are known to infected target computers via corrupted websites and by exploiting browser plugin vulnerabilities. That is the reason why users are often encouraged to update their plugins and extensions regularly. Initially, Trojan Reveton arrives at the system as a random DLL file. Then it drops its own shortcut file in the Windows startup folder, and once Windows starts, the program is executed and the desktop access is blocked.
Ransom collection method
Since FBI Moneypak and other viruses block the desktop, the user cannot use his computer. The user is told that he has to pay the ransom fee to avoid being prosecuted and to unlock his computer. The amount of the fee varies according to the user’s locale and it ranges from 100 USD and 100 euro to 200 Canadian Dollars and 500 Swedish kronor. However, the computer is no unlocked even if the user pays the ransom fee, that is why computer users are strongly discouraged to pay anything.
The distinct feature of FBI Moneypak and other Ukash viruses is that they do not require credit card details. These infections make use of alternative payment systems such as Ukash, MoneyPak and PaySafecard to receive their payments. As a result, even users who do not have bank accounts become subjects to this infection.
Tendencies for 2013
Computer security experts have published quite a few sets of instructions on FBI Moneypak and Ukash virus removal, and it seems that they will still have to work hard on protecting systems from ransomware infections in 2013 as well.
Lately, ransomware infections make use of other distribution methods (such as automated Skype messages, for example), and cyber criminals become more inventive when they need to justify their reason for locking the user’s computer. FBI and the police office are not the only one “responsible” for this anymore. There are various organizations and legal acts such as IRMA, SOPA and PIPA that are held responsible for locking the user out of his computer. The tendency is that Ukash virus is dynamic; it spreads fast, and constantly reinvents itself.
Since we have established that all main computer threats of 2012 come from notorious groups of computer infections, computer users cannot let their guard down, because it is only a question of time when a new edition of Winwebsec, Braviax and Ukash viruses is released.


0 Comments.